
Online Ethical Hacking Course
Our Learners Work at Top Companies
Who Should Join Ethical Hacker Course by EWS Mindcrft ?
Join the best ethical hacking online course by EWS Mindcrft and start your journey in the field of cybersecurity. This course is designed to help beginners understand and master the basics of ethical hacking. You don’t need to have any prior experience in cybersecurity to acquire these skills.
During the ethical hacker course, you will learn concepts like computer networks, cyber attacks, enumeration, malware, ransomware, phishing, attack vectors, vulnerabilities, DoS/DDoS attacks, social engineering, footprinting, sniffing, and much more. You will get to work on several hacking tools and set up an ethical hacking lab for practice.
You’ll get mentorship from experienced professionals who bring real-world knowledge to the live classes. They will guide you through interactive sessions that make learning both effective and enjoyable.
By the end of this online ethical hacking course, you will have a strong foundation that will serve as a stepping stone for more advanced studies or careers in cybersecurity. For more information or details, book your demo class now!
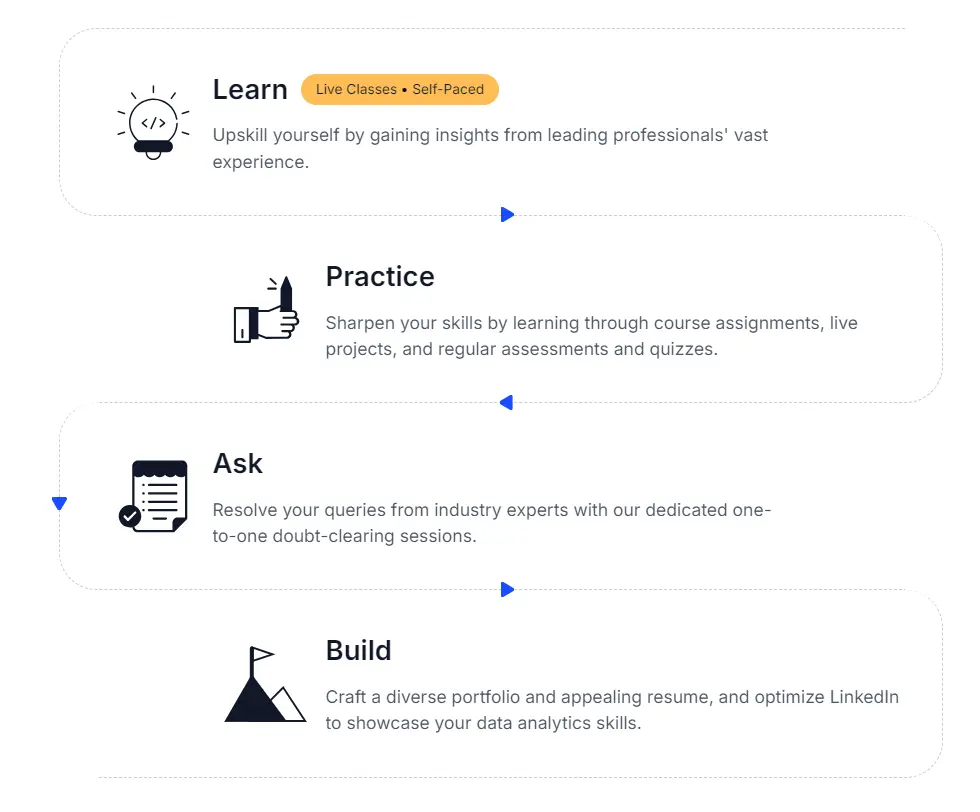
How does this Ethical Hacker course work?
Your Roadmap to Become a Certified Ethical Hacker

Profile-Centric Resume Creation
Craft mrwaint & appeaing resumes
Interview Preparation & Mentorship
Practice with mack interviews, beluse the actual mierview
Internship Opportunities
Bet more exposure & experience with Intemahtas
- Introduction to networking
- Role of networking ports
- Networking concepts
- Networking protocols
- Types of Networking
- What is TCP and how does it work?
- What is ISP?
- Network Protocols
- What is IP address?
- How does internet work?
- Versions and types of IP address
- OSI vs TCP/IP model
- What is MAC address?
- Domain name and DNS records
- Request & Responses
- What is Linux?
- Basic Linux commands (Practical)
- Cool Features of Linux
- Advance Linux commands (Practical)
- Basic File System of Linux
- Getting Familiar with Linux OS
- Setting Up Lab
- Installing Kali or Parrot OS in VMware or VirtualBox
- Install VMware or Virtual Box
- Downloading a good wordlist for Kali Linux
- Introduction to Footprinting & Reconnaissance
- Types of Footprinting
- Website footprinting using Netcraft, Wappalyzer, 3rd party sources
- DNS footprinting using DNSenum, DNS lookup, MX lookup, NS lookup
- Email footprinting using Email Tracker Pro
- Entities of information gathering
- Source of information gathering
- WHOIS footprinting
- Performing information gathering using search engines
- Footprinting through OSINT framework
- Information gathering using Google Dorking and ASO
- Footprinting using Kali Linux
- DNSenum, DNSRecon, Sublister tools for footprinting
- What is network scanning?
- Checking for software with versions
- Network scanning methodology
- OS fingerprinting and banner grabbing countermeasures
- Types of network scans
- Saving XML report for Metasploit & Conversion
- Checking for live systems and Buffer size
- Checking for open ports
- Checking for services on ports
- Introduction to enumeration
- DNS enumeration
- Types of enumeration
- How to enumerate all services?
- Default ports
- Enumeration countermeasures
- NetBIOS enumeration
- SNMP & SMTP enumeration
- NFS enumeration
- Introduction to vulnerability assessment
- Installing Acunetix Pro
- Classification of vulnerability
- Vulnerability scoring systems
- Scanning for vulnerabilities in Nmap scan report
- Vulnerability assessment lifecycle
- Vulnerability assessment using ZAP
- Vulnerability assessment solutions
- Scanning for vulnerability in Nmap scans result (MSF, Exploit DB, Armitage)
- Understanding layers of Internet (Deep, Dark, Surface & Hidden Web)
- Anonymous Configuration in Linux
- Changing User Agent (Random User Agent Switcher)
- Accessing Dark Web (Tor Browser)
- Changing MAC Address (macchanger)
- Creating Dark Web Website (Tor Server)
- Auto Run Shell Script (macchanger)
- VPN & Proxy
- Introduction to System Hacking
- System Hacking using URL
- Cracking Windows Passwords
- System hacking using open ports
- Creating Good Password Lists using Google Dork and Crunch
- URL Masking
- Windows & Linux privilege escalation
- System Hacking using NetCat
- Cracking Windows Password (Pwdump, ophcrack, lophcrack)
- Introduction to Malware
- Static Malware Analysis
- All About Malware Analysis
- Dynamic Malware Analysis
- Example of Malware
- Malware Analysis Tools Practical
- What is Trojan?
- Creating Payloads (MSF)
- What are Viruses and Worms?
- Types of Malware Analysis
- What is Sniffing?
- MAC Spoofing & Flooding
- Active Scanning Techniques
- DHCP Flooding
- Types of Sniffing
- Setup DHCP Rouge (MITM Attack) Using Ethercap
- Protocols Vulnerable to Sniffing
- Sniffing with Wireshark
- Introduction to Social Engineering
- Computer based Social Engineering
- Types of Social Engineering
- Mobile based Social Engineering
- Human based Social Engineering
- Social Engineering Tools
- What is DoS Attack?
- Installing Burp Suite Pro
- What is DDoS Attack?
- DoS in Websites
- What is DRDoS Attack?
- DoS in Networking (hping3, MSF )
- DoS attack using programs and commands (CPU and Memory Utilisations)
- Introduction to Session Hijiacking
- Hijack session using Burp Suite Professional, Ettercap
- How to Perform Session Hijacking?
- Types of Session Hijacking
- Introduction to web servers and web apps
- Web Application Concepts
- Web application hacking methodology
- Vulnerability Scanning using Acunetix Pro, Burp Suite
- Introduction to wireless networks
- Hacking wireless networks
- Types of wireless encryption
- Hacking WEP (Wi-Fi)
- Mobile Platform Attack Vectors
- Using Keylogger App
- OWASP Top 10 Mobile Risks 2016
- Android & IOS Security Scan (MVT, iMazing)
- Mobile Platform Vulnerability and Risks
- Installing Termux on Android
- Calls, SMS, Email Bombing on Android
- Installing Net Hunter Kali on Android
- What is Cryptography?
- Types of Cryptography
- Difference Between Encoding, Hashing & Cryptography
- Cryptography tools
- Introduction to firewall
- GUI Linux firewall configuration
- GUI Windows firewall configuration
- How to optimize your LinkedIn profile?
- How to select a domain in Cyber Security?
- Preparing for job interviews
- Useful resources to keep upskilling

Be in the spotlight by getting certified!
A detailed overview of the course, including key topics, objectives, and module sequence.

FAQs About Ethical Hacker Course
Here’s everything you may ask.
EWS Mindcrft GRADUATES HAVE BEEN HIRED BY



